Typosquatting is a cybercrime technique of making slight spelling alterations in the email address of a company’s employee or CXO to send fraudulent emails in their name. Generally, these minor spelling deviations go unnoticed by the recipients, and they end up getting tricked into sharing sensitive information or downloading malicious files.
Since the typosquatted email address isn’t part of the official SPF record, the email fails the SPF authentication check at the receiver’s end. This way, the fraudulent message either lands in the spam folder or bounces-back, based on what type of fail you’ve set.

Even Barbara Corcoran Was Hit by Typosquatting
In February 2020, Barbara Corcoran, renowned host of Shark Tank, fell victim to a $380,000 typosquatting-based phishing scam. A malicious actor created an email address that closely resembled her assistant’s, with just one letter misspelled. The email contained a fake invoice for $388,700.11 from a legitimate German company, seemingly related to real estate renovations, a field Corcoran invests in. Her bookkeeper, trusting the email’s appearance, wired the money.
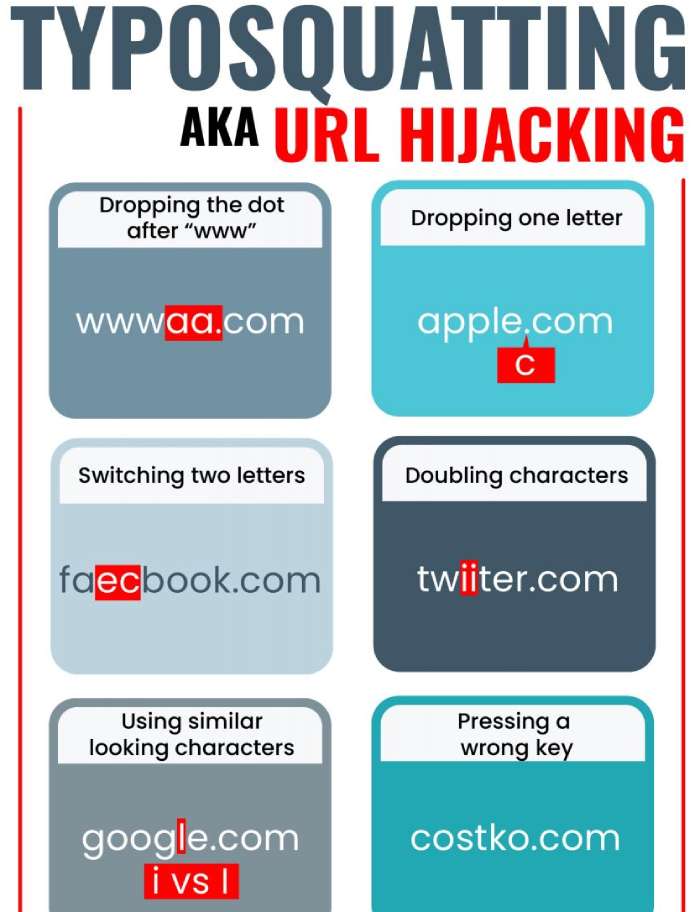
Image sourced from cybersecurityasean.com
The case came to light when the assistant was accidentally included in a reply to the email. While Barbara Corcoran didn’t provide a formal statement, she cautioned against hasty wire transfers via a tweet.
This incident underscores the need for email authentication using SPF, DKIM, and DMARC. Had there been an SPF TXT record (text record) corresponding to their official email-sending domain, the fake email wouldn’t have passed the SPF authentication check at the bookkeeper’s end.
SPF Record Example
Here’s an SPF record example of a string and an explanation of its elements-
v=spf1 a mx ip6:2001:db8:3333:4444:5555:6666:7777:8888 include:_spf.xyz.com -all- v=SPF1 is what every valid SPF record starts with. The v tag represents the SPF version number, and until now, there has been only 1 version.
- The ‘a’ mechanism allows the ip6 address to be a legitimate sender. So, emails sent from this IP address will pass the authentication check.
- The ‘mx’ mechanism tells which recipients are permitted to receive messages for the domain. This tag ensures mail servers managing incoming messages for the domain are also able to dispatch messages.
- 2001:db8:3333:4444:5555:6666:7777:8888 is the IP6 address allowed to send emails from the domain.
- ‘Include:_spf.xyz.com’ indicates that the domain owner has allowed a third-party service provider (having the xyz.com domain) to send emails on behalf of the organization.
- The ‘-all’ tag is used in order to give instructions to receivers’ mailboxes to reject the entry of illegitimate email senders.

SPF Records Best Practices
It’s suggested to create DNS TXT records for all your domains, including the ones you don’t use for sending emails. Threat actors are in constant search of unprotected domains to exploit them to their advantage. Start by enlisting all the IP addresses (IPv4 and IPv6) that you trust and allow to dispatch email messages on behalf of your company, followed by incorporating the right set of SPF record syntax– mechanisms, modifiers, and qualifiers.
If your SPF DNS records have exceeded the lookup limit, then reach out to AutoSPF, where we condense them, which eliminates the need for DNS lookups.
Moreso, it’s vital to run them through credible online SPF record lookup tools that highlight existing configurational and syntactical errors so that you can fix them before mishapening instances. The deployment of SPF, DKIM, and DMARC also improves email deliverability for your email servers.